Information Security
We live in a connected world. It is hard to imagine that what once started as a small number of large computers in the 1970s has grown to encompass billions of connected devices from personal computers and smartphones to Internet of Things (IoT) devices. However, the advent of personal computing has come at the price of additional security risks in everyday life.
The risk of a cyberattack to organizations has increased exponentially. Threats can occur anywhere on the network where there is a potential vulnerability that hackers can exploit, whether through a phishing email message, a fake social media post, or even compromised hardware.

As the number of devices increases, the potential for attacks and disruption grows as well. That is why the need for Information Security measures grows exponentially too.
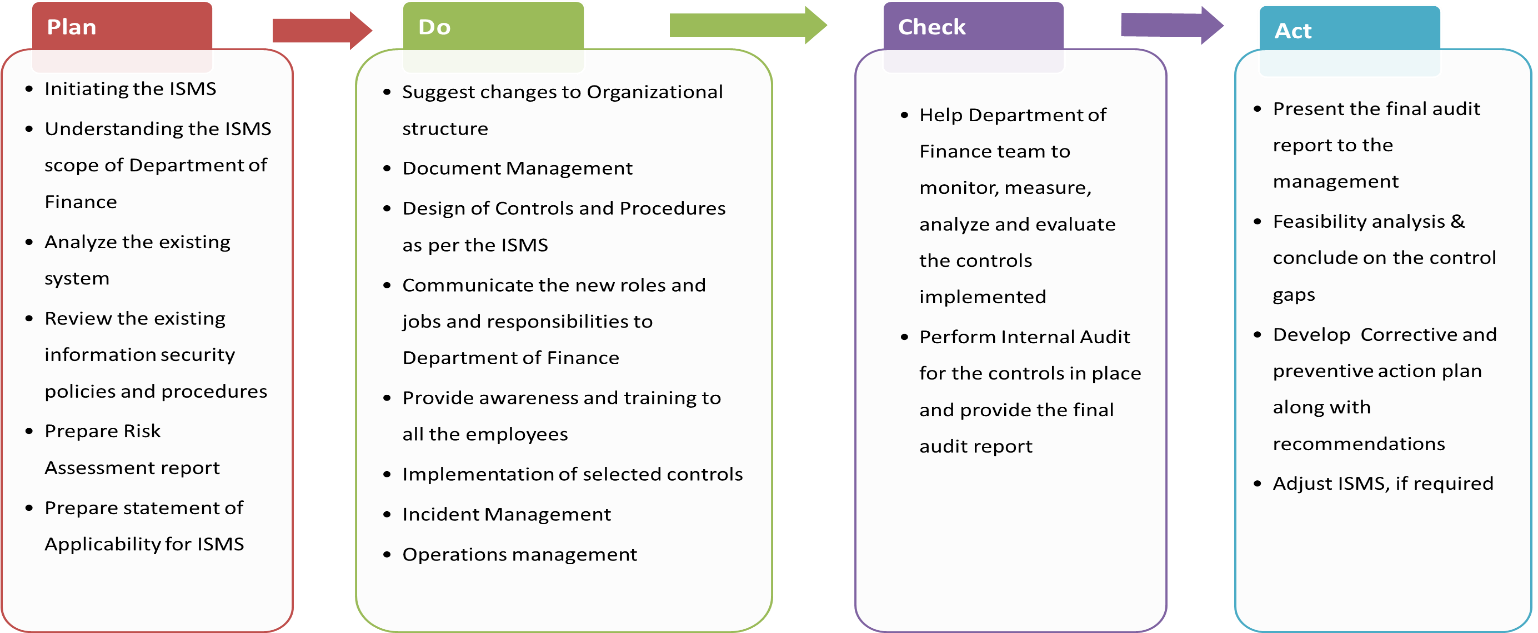
We follow below Approach while implementing the Information Security Standard like:
- ISO 27001
- Abu Dhabi Health Information and Cyber Security (ADHICS)
- National Electronic Security Authority (NESA)
- Information Security Regulation (ISR)
- ISO 22301